Understanding The Complexities Of Software Activation And The Use Of Third-Party Tools
Understanding the Complexities of Software Activation and the Use of Third-Party Tools
Related Articles: Understanding the Complexities of Software Activation and the Use of Third-Party Tools
Introduction
With great pleasure, we will explore the intriguing topic related to Understanding the Complexities of Software Activation and the Use of Third-Party Tools. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Understanding the Complexities of Software Activation and the Use of Third-Party Tools

The digital landscape is increasingly reliant on software, with operating systems and applications playing a crucial role in our daily lives. Licensing and activation mechanisms are essential to ensure software developers receive fair compensation for their work and users enjoy secure, stable software experiences. However, these mechanisms can sometimes present challenges for users, leading to exploration of alternative methods.
One such alternative is the use of third-party activation tools, often referred to as "activators," like the one known as "KMSpico." While these tools may appear to offer a shortcut to unlocking software functionality, it’s crucial to understand the potential risks and ethical implications associated with their use.
The Purpose and Function of Software Activation
Software activation is a process designed to verify the legitimacy of a software license. It typically involves a unique product key, a code that authenticates the user’s right to use the software. This mechanism safeguards intellectual property rights, prevents unauthorized distribution, and ensures access to updates and support.
The Role of Windows 11 Activation
Windows 11, the latest iteration of Microsoft’s operating system, employs a robust activation system that verifies the authenticity of the operating system installation and ensures access to essential features and updates. While legitimate activation methods exist, including purchasing a license or utilizing a digital license linked to a Microsoft account, some users may seek alternatives.
Exploring the Nature of KMSpico and Similar Tools
KMSpico is a third-party tool that attempts to bypass the standard activation process for Windows and Office products. It functions by simulating the activation process, creating a false impression of a legitimate license. While it may appear to offer a convenient solution, it’s important to recognize that using such tools is generally considered unethical and potentially illegal.
Understanding the Risks Associated with KMSpico
Using KMSpico or similar tools comes with significant risks:
- Security Vulnerabilities: Unlicensed software may lack security updates and patches, leaving systems vulnerable to malware, viruses, and other security threats.
- Legal Issues: Using unauthorized software can violate copyright laws and potentially lead to legal consequences.
- Loss of Updates and Support: Users of unactivated software may lose access to crucial updates, security patches, and technical support.
- System Instability: Unlicensed software may not function optimally, potentially leading to system instability and crashes.
- Ethical Concerns: Using tools like KMSpico undermines the efforts of software developers who rely on legitimate licensing to fund their work.
Alternative Approaches to Software Activation
Instead of resorting to potentially risky and unethical solutions, users have several legitimate options for obtaining and activating software:
- Purchasing a License: The most secure and ethical approach is to purchase a legitimate license for Windows and Office products.
- Utilizing a Digital License: Microsoft offers digital licenses that are linked to a user’s Microsoft account. This provides a convenient and secure method of activation.
- Exploring Free and Open-Source Alternatives: There are numerous free and open-source operating systems and applications available that offer comparable functionality to commercial software.
FAQs Regarding KMSpico and Software Activation
Q: Is using KMSpico legal?
A: Using KMSpico or similar tools is generally considered illegal and unethical. It violates copyright laws and undermines the efforts of software developers.
Q: Is KMSpico safe to use?
A: Using KMSpico poses significant security risks. Unlicensed software may lack security updates and patches, leaving systems vulnerable to malware and other threats.
Q: What are the alternatives to using KMSpico?
A: Legitimate alternatives include purchasing a license, utilizing a digital license, or exploring free and open-source software options.
Q: Will I lose my data if I use KMSpico?
A: While using KMSpico itself may not directly result in data loss, the lack of security updates and potential for malware infection can indirectly lead to data loss.
Q: Can I use KMSpico for both Windows and Office?
A: KMSpico is designed to activate both Windows and Office products, but the risks and consequences remain the same.
Tips for Responsible Software Use
- Prioritize Legitimate Sources: Always obtain software from trusted and reputable sources, such as official websites or authorized retailers.
- Understand Licensing Agreements: Familiarize yourself with the terms and conditions of software licenses before using any software.
- Stay Updated: Regularly install security updates and patches for your operating system and applications to ensure optimal security and performance.
- Consider Open-Source Alternatives: Explore free and open-source software options that offer comparable functionality to commercial software.
Conclusion
While third-party activation tools like KMSpico may seem appealing, they come with significant risks and ethical implications. The use of such tools can compromise security, violate copyright laws, and undermine the efforts of software developers. It’s essential to prioritize legitimate and ethical methods for obtaining and activating software, ensuring a secure, stable, and legally compliant computing experience.

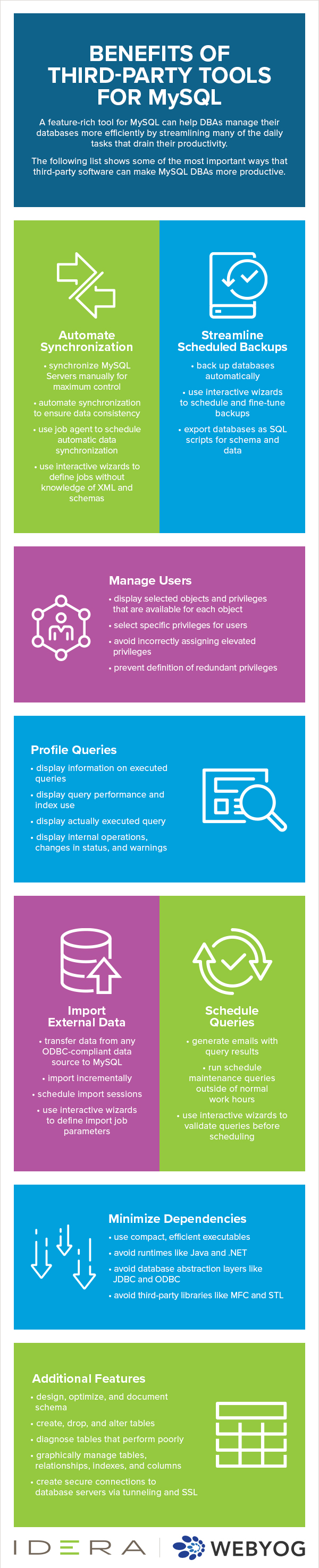

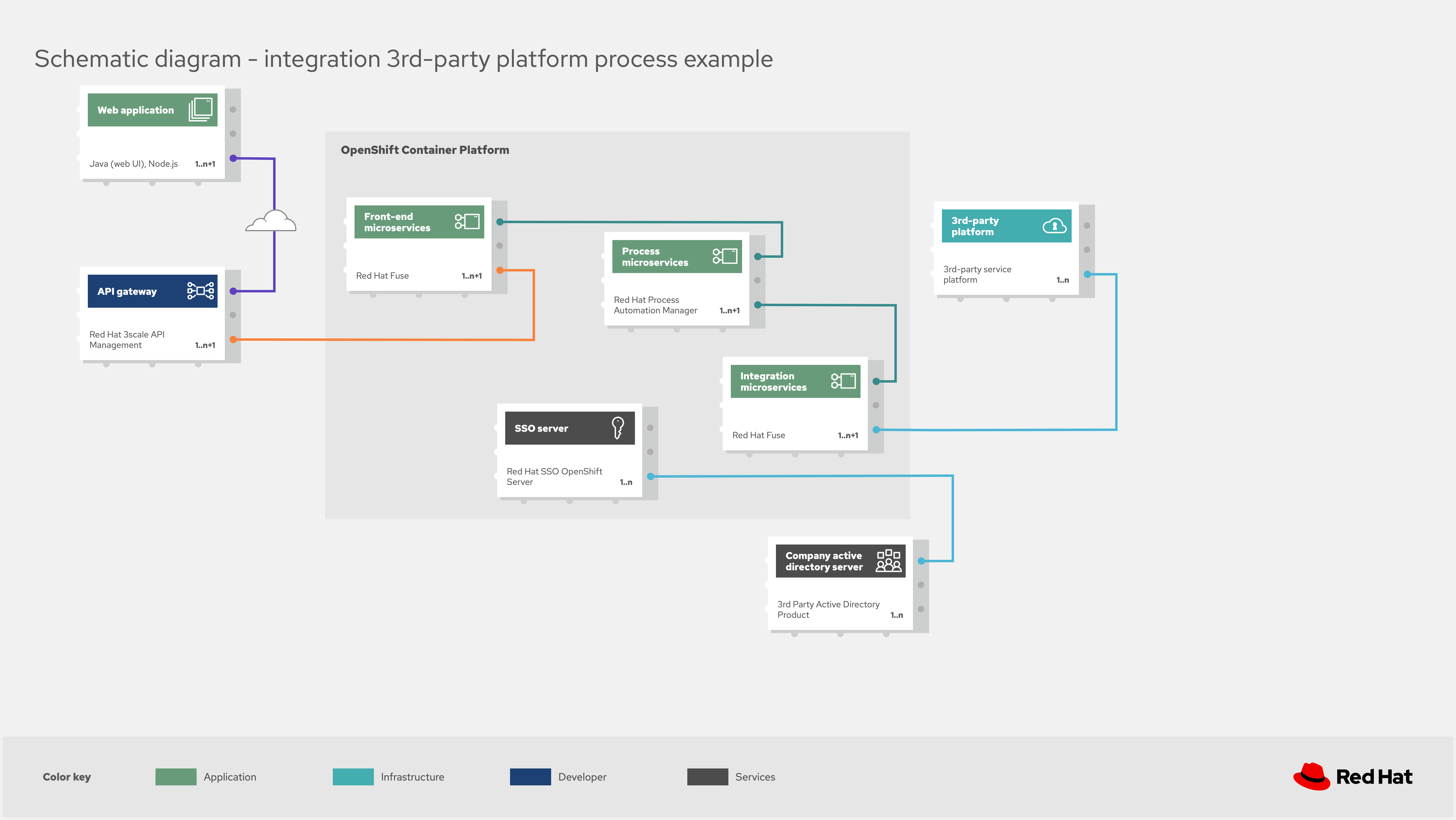
![Salesforce Third-Party Integration: The Complete Guide [2024]](https://exalate.com/wp-content/uploads/2021/08/Salesforce-Third-Party-Integration-01-01-1300x731.png)


.png)
Closure
Thus, we hope this article has provided valuable insights into Understanding the Complexities of Software Activation and the Use of Third-Party Tools. We appreciate your attention to our article. See you in our next article!