Understanding KMS Key Server: A Comprehensive Guide
Understanding KMS Key Server: A Comprehensive Guide
Related Articles: Understanding KMS Key Server: A Comprehensive Guide
Introduction
With enthusiasm, let’s navigate through the intriguing topic related to Understanding KMS Key Server: A Comprehensive Guide. Let’s weave interesting information and offer fresh perspectives to the readers.
Table of Content
Understanding KMS Key Server: A Comprehensive Guide

In the realm of software licensing, the Key Management Server (KMS) stands as a pivotal component, facilitating the efficient and secure management of product activation keys within an organization. This article delves into the intricacies of KMS servers, exploring their functionalities, benefits, and implementation aspects.
What is a KMS Key Server?
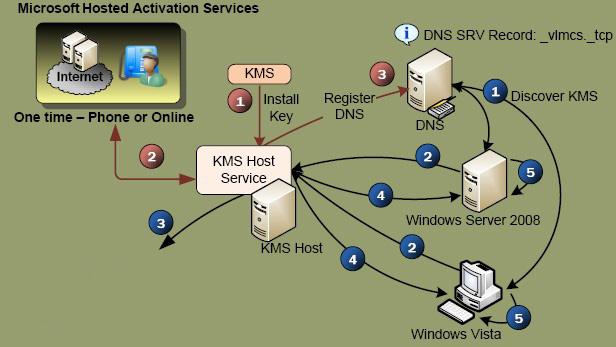
A KMS key server serves as a central repository for product activation keys, enabling organizations to activate their software licenses within a designated network environment. It operates by acting as a central point of contact for license requests, verifying the validity of activation keys, and issuing activation tokens to client machines. This centralized approach streamlines the activation process, reducing administrative overhead and simplifying license management.
Benefits of Utilizing a KMS Key Server
The implementation of a KMS key server offers numerous advantages for organizations:
- Simplified License Management: KMS servers centralize license management, eliminating the need for individual key distribution and activation on each client machine. This streamlined approach reduces administrative effort and simplifies license tracking.
- Reduced Network Traffic: KMS servers act as a central hub for activation requests, minimizing network traffic compared to individual client-to-activation server connections. This optimized communication minimizes network congestion and improves overall network performance.
- Enhanced Security: KMS servers provide a secure environment for storing and managing activation keys, mitigating the risk of unauthorized access or key theft. This robust security framework ensures the integrity of the licensing process and protects against potential breaches.
- Cost-Effectiveness: KMS servers can significantly reduce licensing costs by enabling organizations to utilize volume licensing agreements. These agreements offer discounted pricing for large deployments, making it more cost-effective to license software across an entire network.
- Improved User Experience: KMS servers streamline the activation process, eliminating the need for manual key entry and activation on each client machine. This user-friendly approach enhances the overall user experience, minimizing interruptions and streamlining software deployments.
Types of KMS Key Servers
KMS key servers are available in various forms, each tailored to specific organizational needs and infrastructure:
- On-Premise KMS Servers: These servers are physically located within an organization’s network, offering complete control over the licensing environment. This option provides maximum flexibility and customization but requires dedicated resources for server management and maintenance.
- Cloud-Based KMS Servers: Cloud-based KMS servers are hosted on third-party cloud platforms, providing a scalable and cost-effective solution for organizations with limited on-premise infrastructure. This approach eliminates the need for server maintenance and offers greater flexibility in terms of scaling resources.
- Hybrid KMS Servers: Hybrid KMS servers combine the benefits of both on-premise and cloud-based solutions, offering a flexible approach that balances control and scalability. This option allows organizations to leverage the advantages of both environments, optimizing their licensing strategy based on specific needs.
Implementation Considerations for KMS Key Servers
The successful implementation of a KMS key server requires careful planning and consideration of several factors:
- Network Infrastructure: The network infrastructure must be capable of supporting the communication between the KMS server and client machines. This includes sufficient bandwidth and network connectivity to ensure smooth activation processes.
- Server Hardware: The KMS server requires appropriate hardware resources to handle the workload, including sufficient CPU power, memory, and storage capacity. The hardware specifications should be aligned with the expected number of client machines and the volume of activation requests.
- Operating System and Software Compatibility: The KMS server must be compatible with the operating system and software being licensed. This includes ensuring compatibility with the specific version of Windows or other operating systems being used within the organization.
- Security Measures: Implementing robust security measures is crucial to protect the KMS server and the sensitive licensing information it manages. This includes firewalls, intrusion detection systems, and access control policies to prevent unauthorized access.
- Monitoring and Maintenance: Regular monitoring and maintenance of the KMS server are essential for ensuring its optimal performance and stability. This includes monitoring system logs, performing regular backups, and applying necessary security updates.
FAQs about KMS Key Server
Q: What are the prerequisites for using a KMS server?
A: To utilize a KMS server, organizations require a valid volume license agreement (VLA) for the software they intend to activate. Additionally, the operating system and software versions must be compatible with KMS activation.
Q: How many clients can be activated using a single KMS server?
A: The number of clients that can be activated using a single KMS server depends on the software license and the specific KMS configuration. However, generally, a KMS server can activate a large number of clients, typically hundreds or even thousands, depending on the license terms.
Q: Can KMS servers be used for different software products?
A: Yes, KMS servers can be used for different software products, but each product requires a separate KMS key and configuration. This allows organizations to manage the activation of various software products using a single KMS server.
Q: What happens if the KMS server is unavailable?
A: If the KMS server is unavailable, client machines will attempt to reactivate with the server every 180 days. During this period, the client machines will operate normally, but they will not be fully activated. Once the KMS server becomes available again, the client machines will automatically reactivate.
Tips for Effective KMS Server Management
- Regularly monitor the KMS server: Monitor system logs, performance metrics, and activation activity to identify any potential issues or anomalies.
- Implement robust security measures: Secure the KMS server with firewalls, intrusion detection systems, and access control policies to prevent unauthorized access.
- Keep the KMS server updated: Apply all necessary security updates and patches to ensure the server’s security and stability.
- Maintain a backup of the KMS server: Regularly back up the KMS server data and configuration to ensure data recovery in case of a failure.
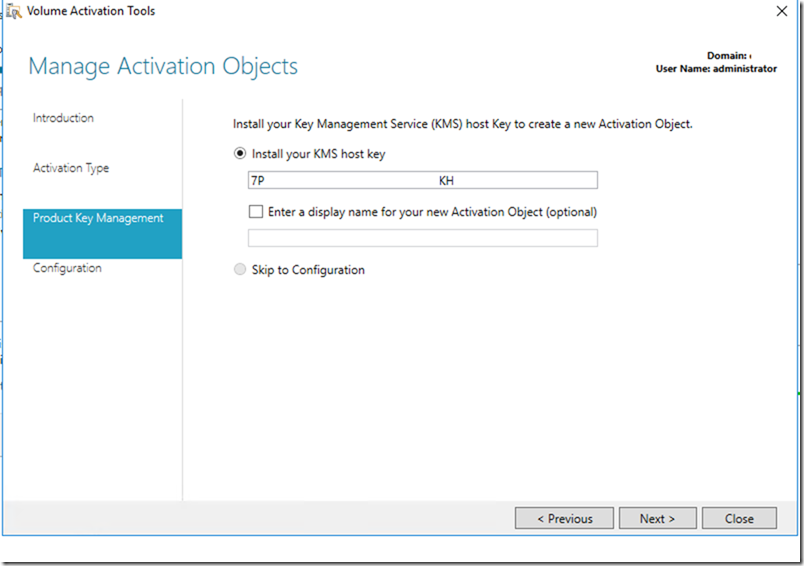
- Document the KMS server configuration: Create detailed documentation outlining the server setup, licensing information, and activation procedures.
Conclusion
KMS key servers play a vital role in simplifying and streamlining software license management within organizations. By centralizing activation processes, reducing network traffic, enhancing security, and improving cost-effectiveness, KMS servers provide a robust and efficient solution for managing software licenses across an entire network. Implementing a KMS server requires careful planning, considering network infrastructure, hardware resources, software compatibility, and security measures. By adhering to best practices and implementing effective management strategies, organizations can leverage the full potential of KMS servers to optimize their software licensing processes and achieve significant benefits in terms of efficiency, cost savings, and security.




Closure
Thus, we hope this article has provided valuable insights into Understanding KMS Key Server: A Comprehensive Guide. We thank you for taking the time to read this article. See you in our next article!